Ambiguity—‘the quality of being open to more than one interpretation; inexactness’.[1]
Numerous modern warfare journals refer to the ‘hybrid’ nature of various aggressors’ contemporary, full spectrum, multi-level strategies and tactics. Stating they are hybrid suggests they are new; they are not. What is new is the use of modern technology to harness information in order to challenge the West in an area it has dominated since 1991 – the information environment. This contemporary strategic theme is thus more accurately described as ‘ambiguous warfare’.
Ambiguous Warfare
Ambiguity is an inescapable facet of the battlespace—actors possess limited intellectual capacity[2]and are subject to numerous physical factors that degrade cognitive faculties, such as emotional responses to the stressors of combat, fog of war, and fatigue. Concomitantly, the ambiguity of information is timeless, subject as it is to numerous simultaneous interpretations, much of these beyond the sender’s control once the information is released. When information is interpreted, it is done subjectively and based on the interpreter’s experiences, group social norms and moral state.[3]This context-dependent co-creation of understanding facilitates the targeting of opponents in the information domain.
Ambiguous warfare aids aggressors’ efforts to locate and degrade their opponent’s centre of gravity (COG). Noting that the West’s COG is seen as the ability to form military alliances to protect vital collective interests, ambiguous warfare targets this capability by infiltrating and delaying decision making cycles. While many threat nations employ authoritarian rule,[4][5]enabling dynamic action at a geo-strategic level, the West is ruled by consensus—delays are therefore common due to the democratic, ‘council’ nature of decision-making. Since ambiguity encourages Western nations to view adversaries as undefined, constantly morphing, unique entities, and since effectively countering threats requires tailored and targeted responses, the introduction of ambiguity exploits such delays to divide public opinion, leading to a greater demand on resources from contributing nations. Such additional demands degrade public (and therefore, political) consensus, manifesting in slower political decision-making.
Information Control Through Media Command
Middle Eastern conflicts over the last three years have illustrated how an aggressor may use its media to aggressively control information about its campaign, telling the wider world one story and its people another. For example, an aggressor may employ state-controlled media to repeatedly highlight the accuracy of its weapons, while in reality many of the munitions dropped or fired are ‘dumb’ and have no guidance systems.[6]Thus, in order to understand the aggressor’s manipulation of the information domain, it is crucial to interrogate how the aggressor has established the context within which their message is delivered. This conceptualisation of the information domain simultaneously acknowledges the need to critically analyse all received data, regardless of any apparent credibility.
The idea of ‘context’ is therefore pivotal to understanding the manipulation of the information domain. Controlling information facilitates state actors’ efforts to engender a desired paradigm in target demographics, a task which subsequently feeds back into further information operations. These methods tacitly accept that information provided to a target audience is liable to proliferate to another audience, often beyond the author’s control and also possibly without their intent. There is an acceptance that the informational effect may evolve both positively and/or negatively;[7]it is this uncertainty that the aggressor relishes, and that the West seeks to avoid at all costs.
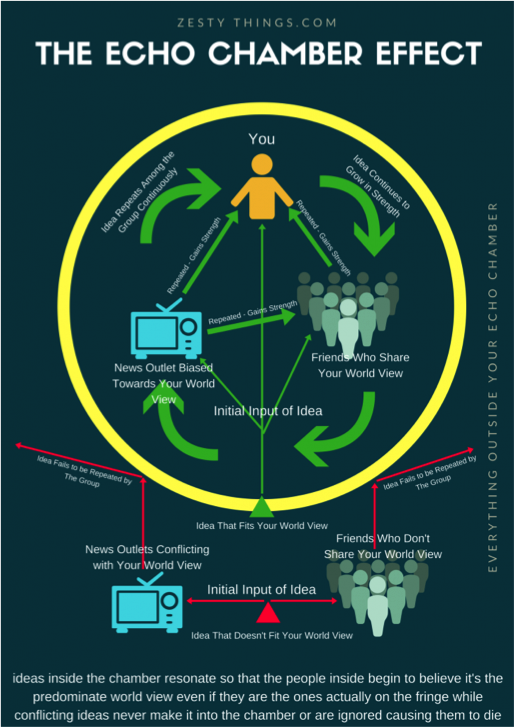
In order to dominate and manipulate the information domain, the aggressor will seek to establish echo chambers[8]at every level. From the geo-strategic to personal tactical, the coordinated messaging at all levels simultaneously strives to reinforce the aggressor’s core messages.
It is crucial to note firstly that every person has a personal echo chamber, one which can be affected if targeted correctly, and that secondly, an aggressor will not necessarily seek to convert others to its own way, but to any paradigm other than that which currently predominates. Business theory conceptualises this in FUD: fear, uncertainty and doubt,[9]a tactic that typically manifests as the spreading of untruths about the competition to undermine consumer confidence in the competitor. In political theory, this is understood as divide and rule.

Manipulating the Information Domain through Cyber Soldiers
To achieve this simultaneous, multi-level messaging, aggressors employ what might be termed ‘cyber soldiers’, a concept that encompasses, but is not limited to: those personnel within aggressor states who operate independently in organisations characterised by decentralised command, such as terrorist cells; activists; NGOs; political/ideological ‘lone wolves’; and other invested international agencies. Importantly, as ‘stateless actors’, modern cyber soldiers have extensive freedoms to prosecute their mission.[10]Unlike their opponents, cyber soldiers are not constrained by international law or obliged to tell the truth, which facilitates their creation and maintenance of an echo chamber designed to pursue targeted objectives.
National organisations are not, however, exclusive customers of such cyber soldiers. Global employment—both state and non-state sponsored—of such individuals is growing, as these assets’ tactical utility becomes increasingly evident through widespread experimentation.
The Information Domain & Mao’s Insurgency Tactics
The scale at which many nations operate is well-known; however, their behaviour in the information domain evinces distinct parallels with Mao’s three-phased insurgency tactics,[11]comprising organisation and preparation, terrorism and guerrilla warfare, and conventional warfare.
Phase One – Organisation and Preparation
In Phase One, the enemy seeks to set conditions that are favourable in an as-yet unrealised battle space. Preparing the ‘cyber ground’ is facilitated by the numerous capable organisations that have been born from the shift in information warfare, both nationally and internationally. Thus, information is fed into echo chambers already established in target audiences—audiences delineated by country, social demographic, age, or social media channel, to name but a few—introducing, reinforcing, or manipulating narratives depending on the mission. The process occurs at a time of the sender’s choosing, with the mission’s time scale often irrelevant, varying from hours to years.
The preparation conducted by cyber soldiers relies on the fact that information must remain relevant to the target audience,[12]sometimes even allowing counter information to propagate and ‘trend’ in the information space. Context is subjective. A simple example is the use or misuse of punctuation: the panda eats, shoots, and leaves, versus the panda eats shoots and leaves. Context one is violent and loud, the second, simply calorie consumption. Correct punctuation is now almost voluntary[13]and with its decay, misunderstanding spreads and leads to ambiguity.
Syria provides a good example of the implementation of Phase One during an informational conflict. After years of conflict, many media users were ready to support anyone with a consistent and believable message, no matter how abhorrent it might be, a situation well understood by key organisations in Syria.[14]Simultaneously, though chemical weapons employment was a ‘red line’ for President Obama’s administration[15]that carried clear repercussions, the US took little recognisable actions after numerous chemical attacks on civilians. Such inconsistent messaging weakened the US’s position in Syria, compounded by a complicated Western diplomatic position that remained unconvincing to the Syrian population. National organisations took advantage of this ambiguity, synchronising their own information strategies and campaigns to deliver compelling and convincing arguments, and followed their claims with physical actions. This linkage of the physical and informational domains gave the aggressor more credibility and a larger share of the regional audience.
Phase Two – Terrorism and Guerrilla Warfare
In Phase Two, the enemy employs terrorism, ‘the unlawful use of violence and intimidation, especially against civilians, in the pursuit of political aims’.[16]Such action, typically executed at a time when the opponent’s focus is elsewhere, prepares the ‘ground’ for further action. Phase two is dominated by the aggressors use of Terrorist or Guerrilla activities in support of its aim. The aim of phase two is often, but not confined to, finding the opponents weaker areas or forcing the opponent to spread their forces so thinly that the opponents force becomes fixed, offering opportunities for the aggressor to attack. This is exemplified in the initial deployment of an aggressor’s “grey forces”[17]during a land grab, which is evident throughout history. Thus, the Ottoman Empire employed its spy network ahead of its main force advance to out manoeuvre or deceive their enemies. Contemporary conflicts similarly demonstrate situations where ‘unattributed’ forces are used to set the ground—ironically when the ground is set, it often manifests itself as near-chaos or confusion amongst the opponent’s population or personnel.
In the information domain, such terrorism operates through the ‘weaponising’[18]of information, which facilitates the continuous dynamic targeting of an adversary’s moral component. The reach of such methods is almost unlimited as global information consumption increases. Western societies’ marginal appetite for foreign intervention thus not only empowers aggressors to pursue expansionist methods against its neighbours, but also facilitates these actors’ manipulation of information both locally and globally. Accordingly, strategic action is supported by the new and novel cyber soldiers. Targeted at the tactical level (individuals or small groups), methods such as extortion, kidnapping, and bribery are highly effective, thanks in large part to today’s highly-mediated information space.
Phase Three – Conventional Warfare
Phase Three emphasises conventional warfare, manifesting in the information domain as once-secondary news outlets taking on, and defeating, established outlets. As part of this, the aggressor will use its strengths against the opponent’s weaknesses. For example, Irish media organisations are liable for any information found to be wrong or misleading; the aggressor, however, is not constrained by the same laws. The aggressor can thus exploit the opponent’s perceived weakness by publishing so much contradictory or counter information that the truth is buried deep within the massive influx of information—an avalanche of data that an average person is not equipped to make sense of.
The global population in the cyber and information domains (both of which remain conceptual),[19] is indirectly affected by the enduring nature of economic war.[20]And, while economic warfare is a strength and thus key tool of conventional warfare for the West, this is not true of most other states. An aggressor will thus rarely commit to a “Black Swan”, recognising the capacity of levers such as UN and EU sanctions to have a debilitating effect on a national economy.
Simultaneously, the virtual domain (which includes cyber activities) enables a new form of warfare, not visible to many, to be waged at scales that are unimaginable. The modern aggressor lacks a physical presence, meaning any act is often difficult to attribute in a timely manner to an individual, let alone a state.[21]During the Cold War there were proxy conflicts, conventional by nature but detached from the superpowers’ populations by geography. We see the same today in Georgia, Ukraine, Moldova, Yemen, Syria, Lebanon and Libya, among others. The superpowers are often on opposing sides, both geographically and ideologically; however, the effect of geography is negated more than ever due to the speed at which information proliferates.
Critically, as Mao did, when the aggressor finds a weakness in the information space it exploits that opportunity. When the aggressor finds strength it adapts, harassing and seeking another avenue of attack—changing its narrative until it finds traction. This tactic allows the aggressor to out-manoeuvre its foe in the information space, leading to the erosion of public confidence in leaders and organisations, paralysing the enemy’s decision makers.[22]CGS’s January 2018 RUSI speech,[23] spoke about the speed of recognition, the speed of decision-making, and the speed of assembly: one of the first commanders to recognise this need in the information space. Without it, we will give all aggressors a victory, potentially before Western soldiers leave their barracks.
Cyber and Joint Action in Future Conflict
As technology continues to advance, the role of the information domain in future conflicts will continue to develop, shaping the manifestation and conduct of warfare. The Future Force Concept (FCC)states:
In particular we lag well behind in our ability to exploit the information environment and in the full integration of space and cyber domains.[24]
Thus, enabling joint action across the five domains (Air, Land, Sea, Space and Cyber) is the baseline for operations in all future conflicts. Harnessing the capabilities of the cyber domain is fundamental to this outcome, seen across different areas of the battlespace.
Cyber in The Deep Battle
The UK’s layered operational design eases planning from BG to Army level by dividing the battle space and giving each an area of responsibility. The key is the deep battle, where a numerically superior enemy is degraded to enhance the likelihood of friendly force success. How do you use cyber/information in the deep battle? Assuming most conflicts will be either littoral or urban due to population dispositions, the ability to control and manipulate physical traffic patterns provides a simple example.[25]To hamper an enemy’s logistics, a commander may attack convoys from the air; however, the air domain is contested by 5th generation aircraft on both sides and attacks may be costly.[26]Therefore, the commander may instead change traffic patterns. Sowing chaos into the civilian population and consuming more of the enemy’s precious combat power, the change in traffic patterns thus forces the enemy to reallocate resources in an effort to ensure MSRs are kept clear. Add a localised misinformation campaign, and the enemy could face choreographed chaos in the population and simultaneously, in some cases, amongst its own troops. The enemy is thus subjected to ‘Black Mist’ – the temporary psychological disorientation of a group through the delivery of deliberately ambiguous information to create chaos (controlled or otherwise) giving the friendly commander time to act.[27]
Targeted Misinformation Campaigns
Most aggressors’ strengths lie in their patience and ability to collect information. For example, NATO eFP BGs were subjected to misinformation campaign after the North Atlantic Council announced the BGs would receive the Freedom Award in 2017.[28]A state-controlled channel subsequently released an article maligning the BGs. It stated that, over a one-week period, BG soldiers had been caught drunk, caused damage to public property, rolled a vehicle and finally been shot at by a local farmer during a pan NATO exercise. Yet the events highlighted took place over four months, not seven days,[29]and the details of such events were and still are mis-reported. Though the story gained little traction across the originators’ internal audiences and failed to proliferate into Western media (after a week it had little more than 300 shares on Facebook[30]), this example demonstrates the gathering and timely use of information to target an opponent.
The MoD and NATO did not counter the article publically. The reason? Basic botnets are/were, on average, between 150 and 400 ‘profiles’ in size;[31]it was therefore assessed that the content was circulated by a botnet with very little human interaction. Countering the story would have compounded its effect and provided the conduit for the message to reach audiences it would not have otherwise.
Friendly Force Messaging Operations
Information operations are the marketing of an idea,[32]and thus, by their very nature, are both dependent upon, and influence, context. Thus, NATO and Allied messaging must be timely and targeted in order to be effective. This precise level of detail and its timings enables planners to focus on incremental gains that, when arranged in tandem with conventional operations, not only enable manoeuvre but also prepare the ground for future operations. Yet ambiguity is not always misinformation. Indeed, as noted earlier, ambiguity has long been an inescapable part of the battlespace, and given human fallibility, will inevitably remain so. Utilising ambiguity in the face of the enemy will be a significant capability in future deep operations, its utility extending from the reinforcement of tactical deception to the enabling of strategic dialogue (from feints to peace talks).
Ambiguity is timeless, unconstrained and is subject to simultaneous interpretation, inherently at odds with people’s view that everything has constraints. Thus, though it is assumed that when the truth is established, the discussion is complete, today’s aggressors will continue narratives past the point of truth to create ambiguity, which can then become self-perpetuating. Accordingly, just as intelligence has counter-intelligence, so too must future information operations.
To combat A’s implication of a unique relationship with N, a cross-government/holistic alliance response from FF is necessary. Emphasising the pre-existing relationship between N and FF inherently undermines A’s message, encouraging consumers to investigate alternate views. This sequence of events thus exemplifies counter-information operations.
Even so, some audiences remain incredibly difficult to reach. These are populations that fundamentally believe messages they receive from the aggressor. Through long term planning and better targeting, the selected audiences can be equipped with the tools to look elsewhere for their alternative truths.
Countering Ambiguity in Warfare
Ambiguity will endure; however, the weaponised form used by various aggressors can be countered in a number of ways. The first is by controlling the context in which information is interpreted. For an aggressor to succeed it doesn’t need to convert audiences to its worldview, simply any other than the current paradigm, effecting the premise of ‘divide and rule’. Western interaction with its aggressors must therefore be targeted to avoid the reductive generalisations that assume the aggressor is one homogenous mass and are liable to induce ill-will in civilian populations. This is especially true when considered in light of the aggressor’s more sophisticated and personalised approach, which singles out organisations or people to create a feeling of uniqueness and thus improved receptivity. Aggressors are successful because they subtly signpost the audience’s attention to where they want it to be, manipulating and misinforming as needed.
Secondly, the friendly alliance must continue its transparency when combating ambiguity. The alliance must avoid criticising aggressors as a whole nation and instead target and refine responses far more effectively, failing to do this highlights insecurities and a fundamental lack of understanding of an aggressor and it’s people. In many of the aggressor’s politics, a strong nation is seen as a stabilising force in the world. They will only be content when the aggressor feels respected by the rest of the world.
Lastly, the West must be equipped at every level to co-ordinate efforts and embrace the complexity of ambiguity. As the Chief of Swedish Defence Forces, Major General Karl Engelbrektson, stated, ‘war is a contest of will’;[33]or, as stated by General John ‘Mick’ Nicholson ‘war is staying power’.[34]Maintaining public support is crucial as it is indivisible from political will. The five domains must act in synergy across all military, government and alliance levels to contest and win future conflicts. The information war manifests itself as the passage of information, by any means, to the public on both sides of future conflicts. Owning at least part of this domain will affect all future conflicts and should be a key tenant of strategic planners.
About the Author
Captain Robert Atchison is a British (Royal Armoured Corps) officer posted to HQ ARRC, who has deployed to Afghanistan and Estonia as part of ongoing NATO missions.
Endnotes
[1] Definition provided by Google define.
[2] The Intellectual “Bell Curve”.
[3] “Seeing is believing: 5 studies about visual information processing” Articleby Will Fanguy.
[4] Global State article, “Putin’s new authoritarian Russia”.
[5] Article– Authoritarianism and Foreign Policy: the twin pillars of a resurgent Russia.
[6] The Guardian article, “Russia suspected of using dumb bombs…Syria War Crimes”.
[7] Article – “Retaking the high ground” by Dennis Gibson and Stephen Moore.
[8] Forbes Article – Are You In A Social Media Echo Chamber? How To Take An Objective Look.
[9] Changing Minds Article – Fear, Uncertainty and Doubt (FUD).
[10] Time Article – This KGB Chief Rang the Alarm About Russia-U.S. Cyberwars. No One Listened.
[11] Parallel narratives Article – “The three stages of Mao’s revolutionary warfare”.
[12] Entrepreneur Article – How Marketers Must Evolve to Remain Relevant in a ‘Post-Millennial’ World.
[13] Seen in today’s printed press headlines – http://littlecalamity.tripod.com/Text/Newspaper.html.
[14] Post operation interview with Capt Richard Luckyn-Malone 77X.
[15] Business insider Article.
[16] Google definition.
[18] The menace of unreality: How the Kremlin weaponizes information, culture and money – Article.
[19] Nearly impossible to define in a physical sense or make easily relatable.
[20] Building a win-win world: Life beyond global economic warfare, H. Henderson.
[21] Article– “Attributing cyber-attacks”, journal of strategic studies 2015.
[22] “Manipulating the ooda loop: the overlooked role of information resource management in information warfare”, thesis by Gregory M. Schechtman Captain, USAF.
[23] Speechfrom UK CGS, Gen M Carleton-Smith RUSI 2018
[25] Human, ground vehicles, aircraft, shipping, etc.
[26] Future Air and Space Operating Concept – UK Gov.
[27] Author defined.
[28] Sputnik article“ Medal for Knavery, Estonia to award rampaging NATO troops with military honours”.
[29] Author was manager of event in 5 Rifles BG and tracked live media feeds.
[30] Author’s research during event.
[31] Author worked with EST, UK and FRA OGDs on assessment.
[32] “What exactly is marketing ops?” Econsultancy Article.
[33] Speech as part of the 2018 International Armoured Vehicles Conference London.
[34] During Gen Nicholson’s speech on Op INHERENT RESOLVE during the 2018 International Armoured Vehicles Conference London.